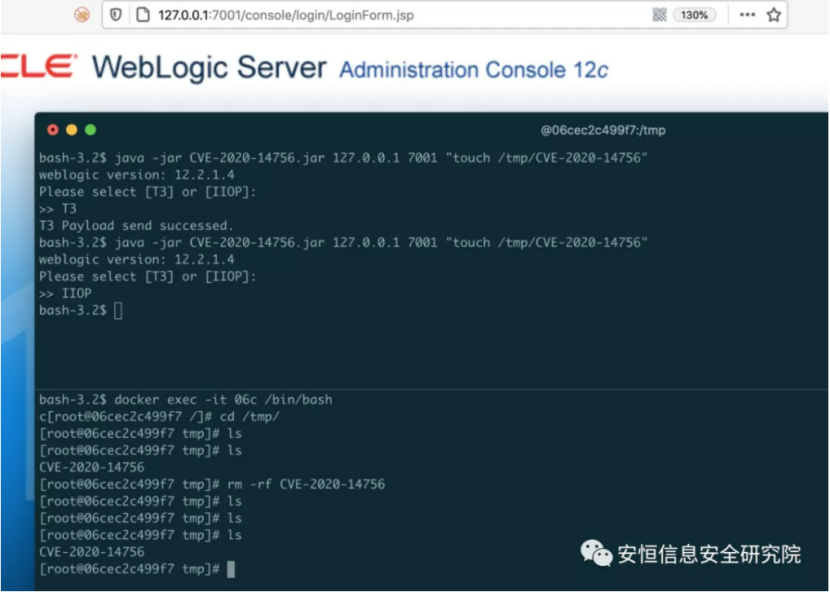
Screenshot of Vulnerability Repetition Proof
Scope of influence
Oracle Weblogic Server 12.1.3. 0.0, 12.2. 1.3. 0, 12.2. 1.4. 0, 14.1.1. 0.0
Vulnerability Analysis
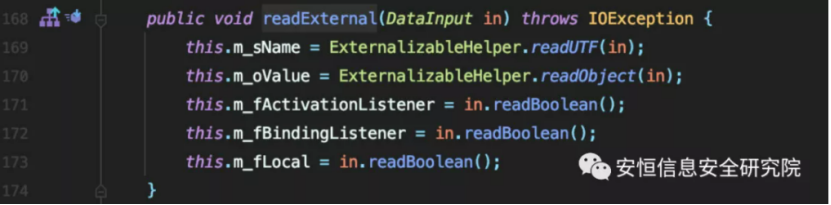
There is an interface com.tangosol.io.ExternalizableLite in the Coherence component, which is similar to java.io.Externalizable. It inherits java.io.Serializable and has two methods to implement: readExternal and writeExternal.
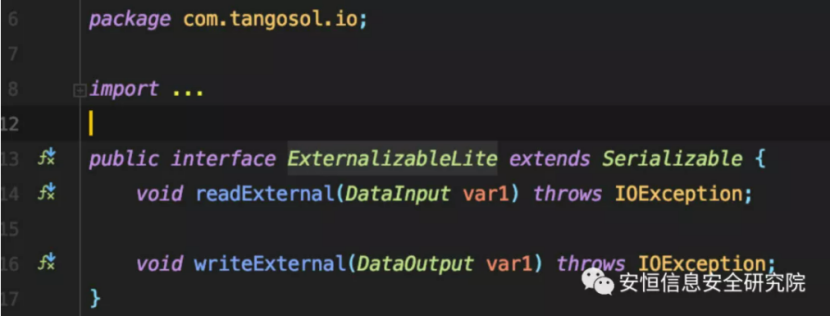
This interface implements the readExternal and writeExternal methods of the class for custom serialization and deserialization with the help of ExternalizableHelper.
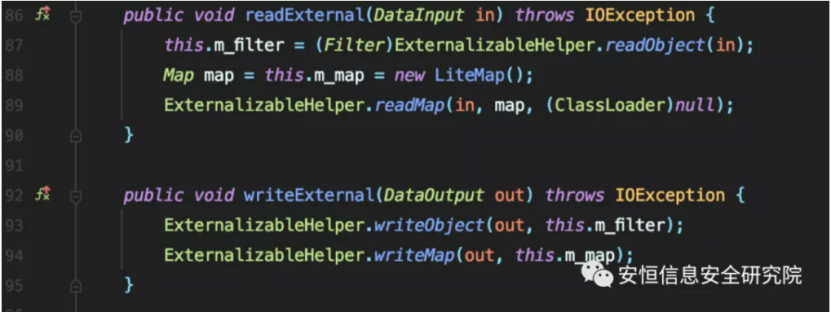
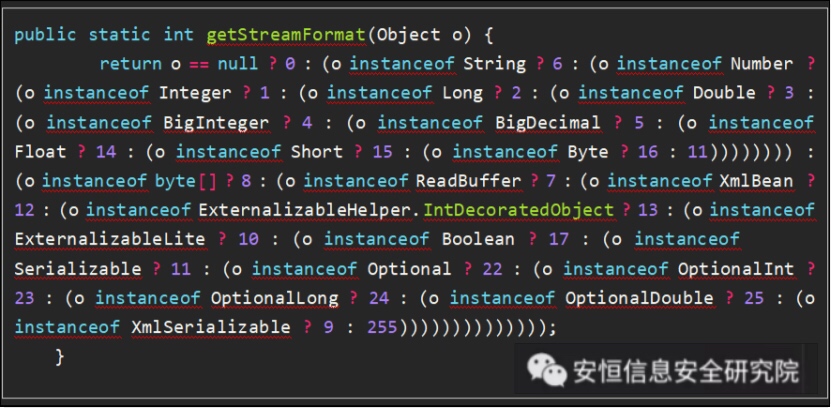
Let’s take a look at the readObject method of ExternalizableHelper.
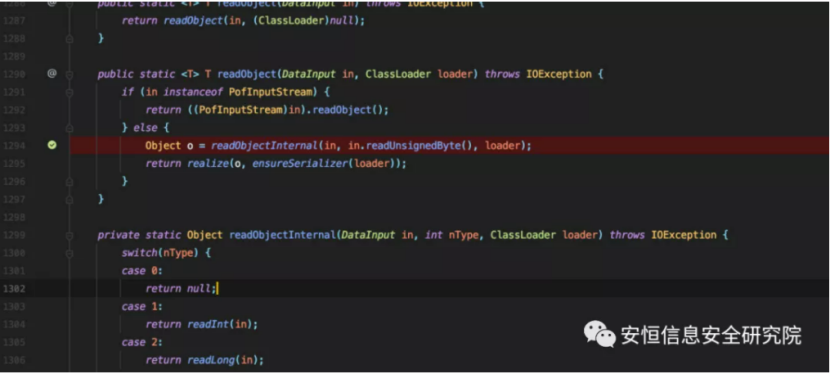
ReadObjectInternal calls different read methods to deserialize according to different nType data types, which represent data types that correspond to the number returned by the getStreamFormat method when wrtieObject serialization is called.
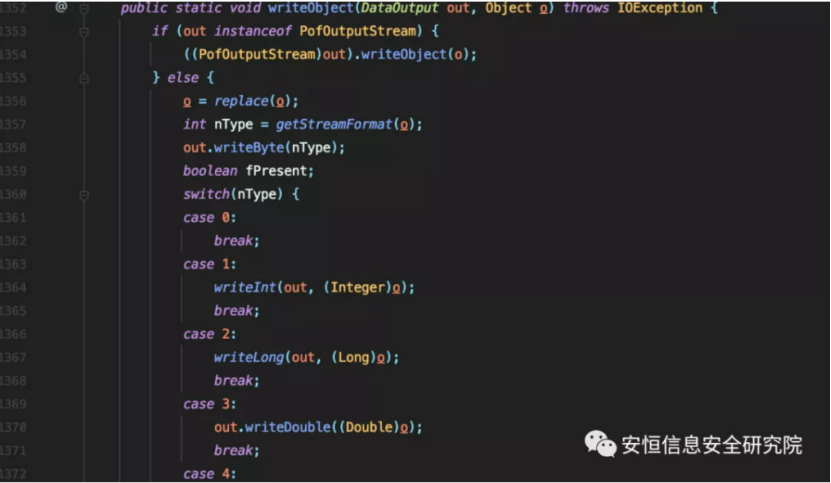
Follow up the readExternalizableLite method, which is used to deserialize objects that implement the java.io.ExternalizableLite interface.
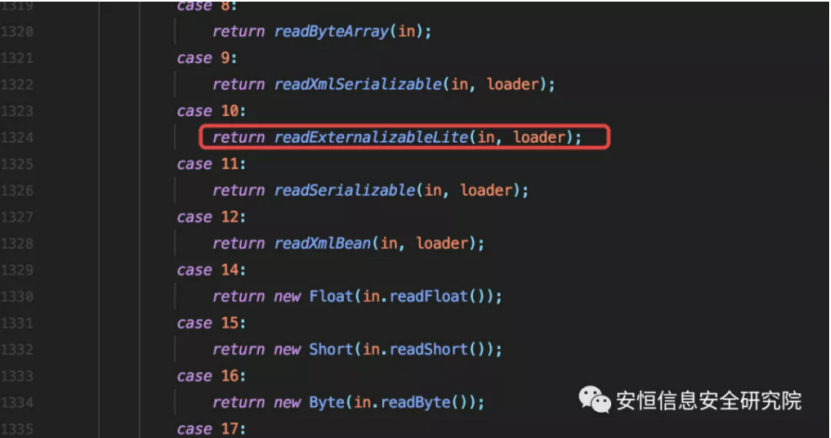
The method loads and instantiates the class name written on serialization and calls its readExternal method.
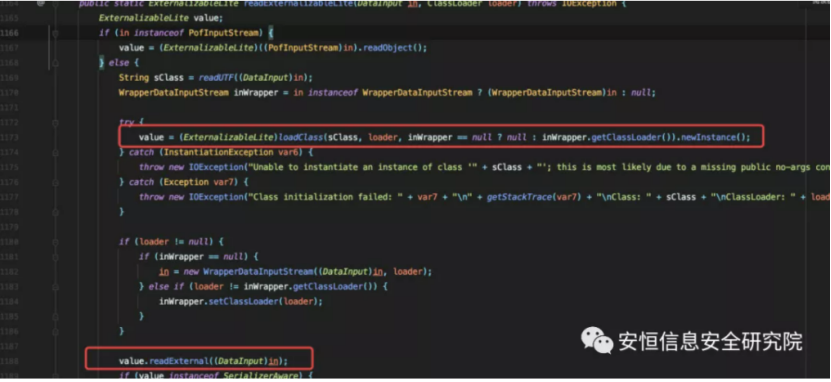
Weblogic filters deserialized classes when the class is loaded, so classes loaded in readExternalizableLite are not restricted by blacklists.
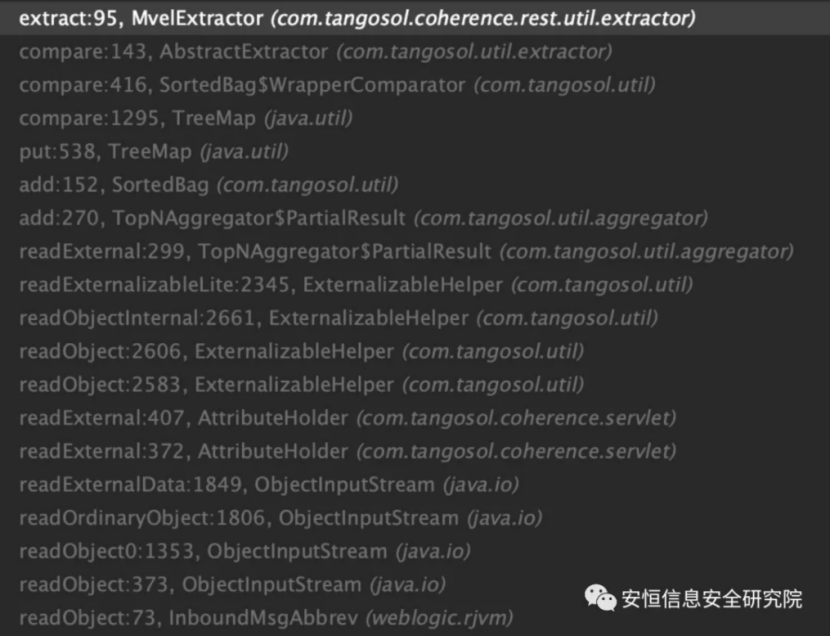
That is to say, we can now call the readExternal method in the blacklist class. The author used com.tangosol.coherence.rest.util.extractor.MvelExtractor, which was used in the previous vulnerability, and implemented the ExternalizableLite interface.
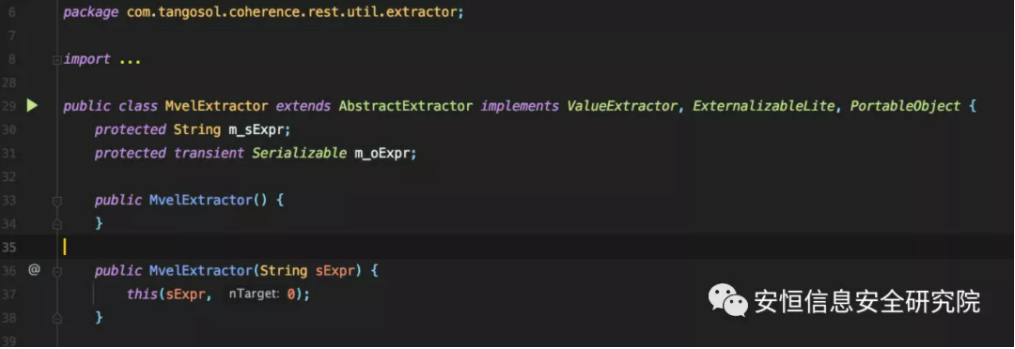
Its extract method can execute MVEL expressions, so long as we control this.m_sExpr is the expression we want to execute.
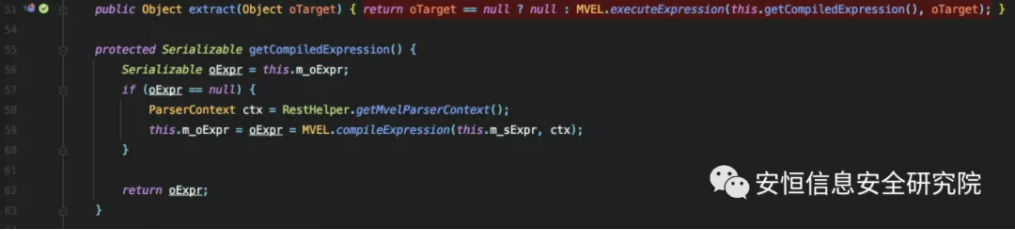
Its readExternal method assigns a value to this.m_sExpr, and we can control it, so as long as we can call its extract method, we can execute arbitrary code.
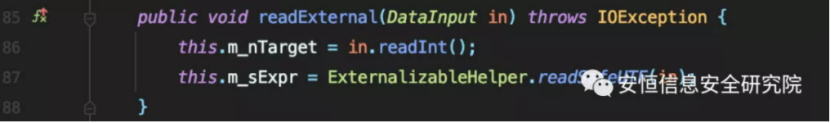
The author found the readExternal method of com.tangosol.util.aggregator.TopNAggregator.PartialResult.
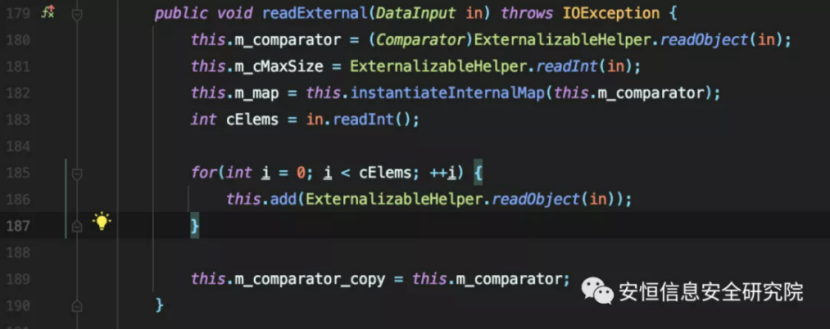
This.instantiateInternalMap (this.m_comparator) assigns the TreeMap’s comparator attribute to new SortedBag.WrapperComparator (comparator), which we can control to be MvelExtractor.
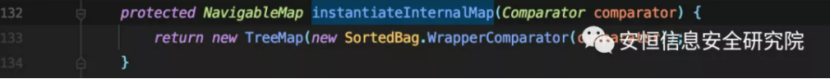
Follow up super.add (value)
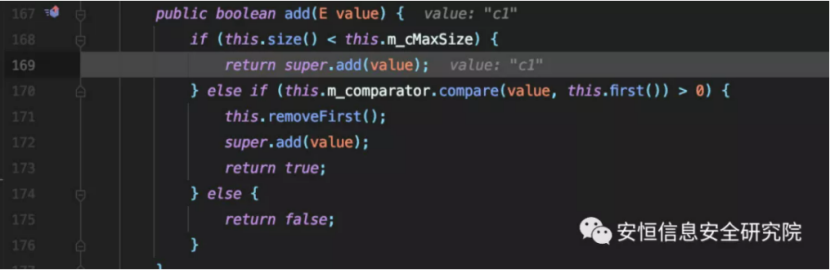
Eventually, map.put is called, and the map is the TreeMap object assigned above.
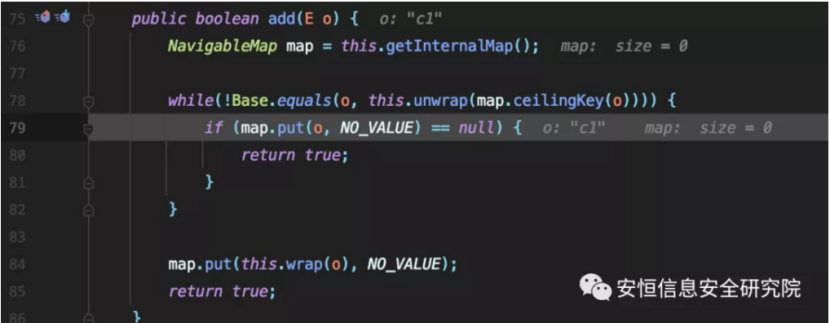
Follow up its compare method.
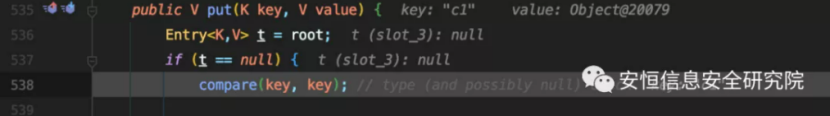
The Compare method of SortedBag.WrapperComparator is called here.
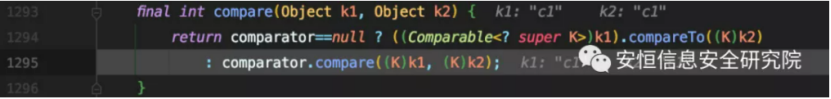
Finally, this.f_comparator.compare is called, and this.f_comparator is the MvelExtractor object.
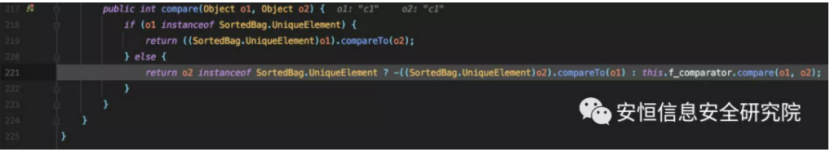
Follow up to the compare method of MvelExtractor parent class com.tangosol.util.extractor.AbstractExtractor # compare, where the extract method of MvelExtractor is called and any MVEL expression is finally executed.
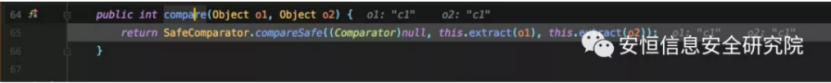
However, the readExternal method of com.tangosol.util.aggregator.TopNAggregator.PartialResult is not called by default because it does not implement the ExternalizableLite interface, so you need to find another class that implements the Externalizable interface and can call the ExternalizableHelper.readObject method.
The author found com.tangosol.coherence.servlet.AttributeHolder
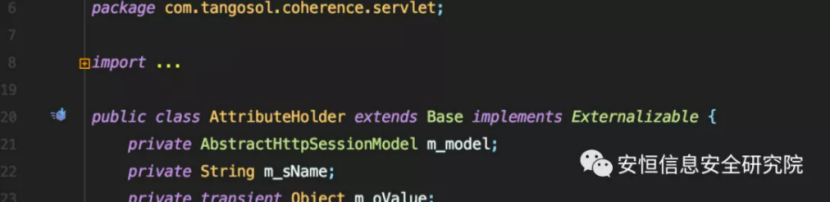
ExternalizableHelper.readObject (in) is called in its readExternal method.
Call stack
Vulnerability Repair
- Install the latest patches.
- Detect and defend this vulnerability through DAS-Security related products.
- Disable T3, IIOP protocol.
Author
Smi1e@WEBIN.LAB - DBAPPSecurity