Screenshot of Vulnerability Repetition Proof
Scope of influence
Oracle Weblogic Server 12.1.3.0, 12.2.1.3, 12.2.1.4
Vulnerability Analysis
com.tangosol.util.ExternalizableHelper#readXmlSerializable will pass the sXml read by deserialization into (new SimpleParser()).parseXml for XML parsing.
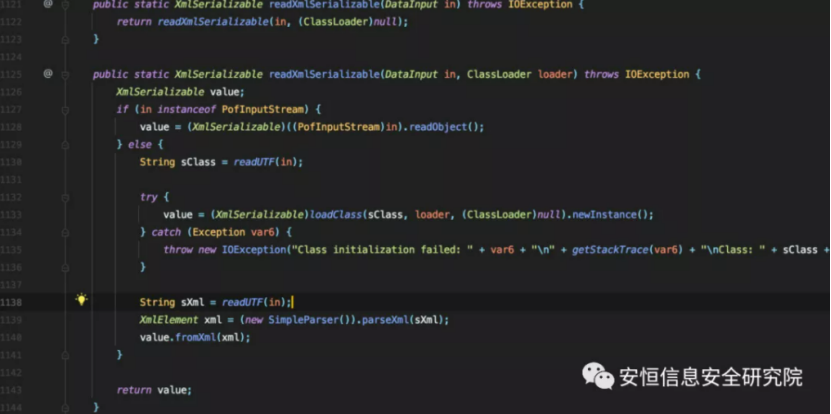
Following parseXml, this.parseDocument (xml) parses the xml string we passed in into an XmlDocument object.
If this.m_fValidate is true, call (new SaxParser ()). ValidateXsd (sXml, xml) validates the xml format, which is true by default.
Following the validateXsd method, the XXE vulnerability will eventually be triggered by a call to validator.validate (source), which is the source object of the xml we passed in. But only if listSchemaURIs are not empty.
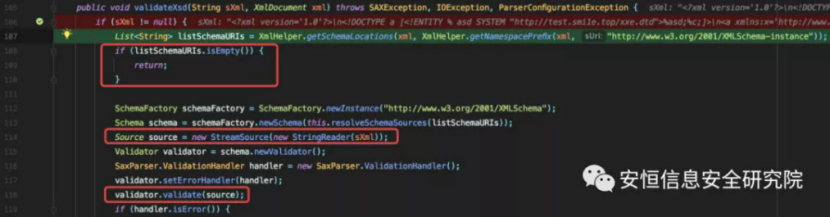
Take a look at the assignment process for listSchemaURIs
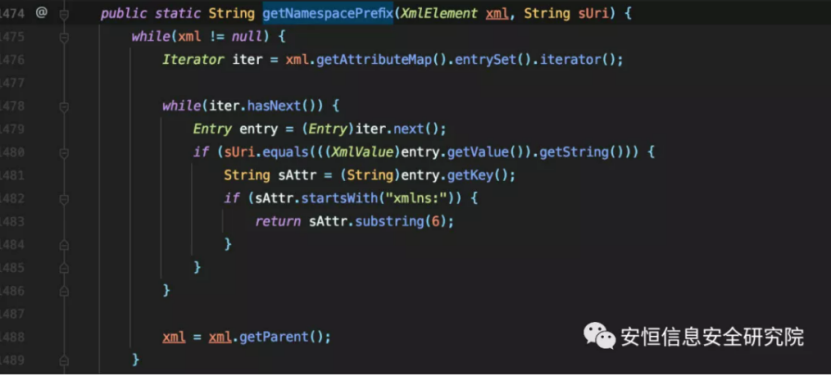
XmlHelper.getNamespacePrefix gets the label attribute that starts with xmlns: and returns the string following it as the prefix.
XmlHelper.getSchemaLocations extracts the value of prefix +: schemaLocation or: noNamespaceSchemaLocation, splits it by whitespace and adds it to listURLs every two bits.
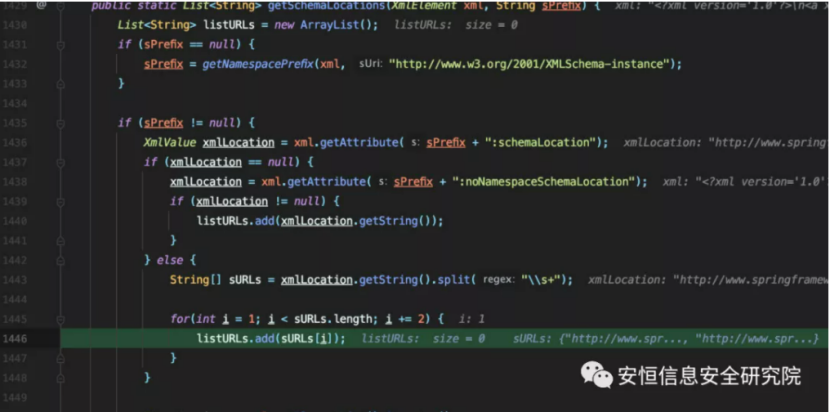
Therefore, we construct the following format to make listSchemaURIs not empty.
1 | |
Follow this.resolveSchemaSources (listSchemaURIs),
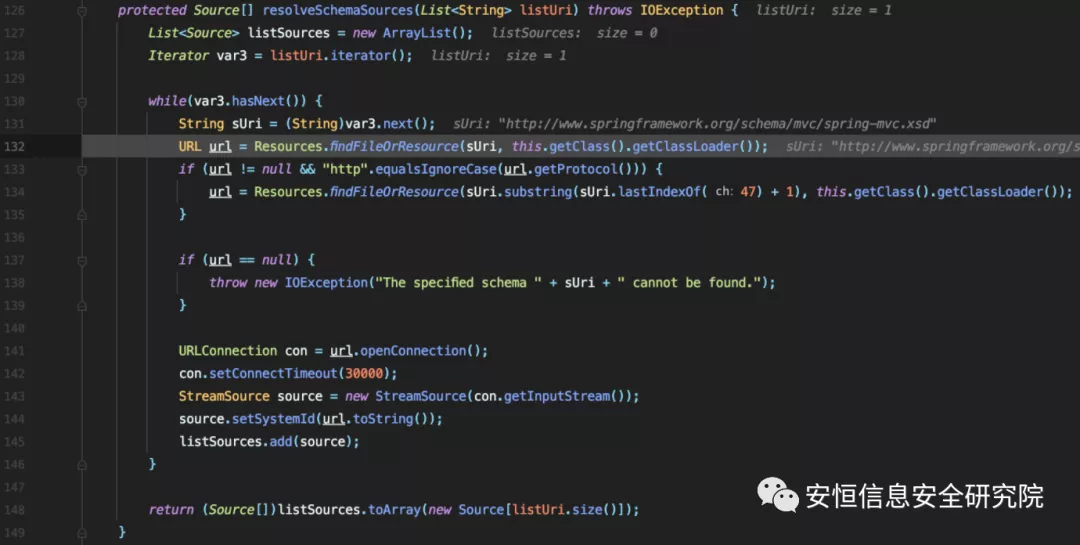
AppCLassLoader will eventually be called to find the resource file in the URI locally instead of loading it remotely.
So we need to find a workable XSD file locally, and I’m using coherence-rest-config. Xsd from Coherence.jar, so replaces http://www.springframework.org/schema/mvc/spring-mvc.xsd with http://www.springframework.org/coherence-rest-config.xsd.
Finally, we still need to go to the deserialization entry in com.tangosol.util.ExternalizableHelper # readXmlSerializable, which can also be used with CVE-2020-14756. The corresponding nType of com.tangosol.coherence.servlet.AttributeHolder readXmlSerializable is 9.
We can override AttributeHolder’s writeExternal method and write the custom XML directly according to the reading process during deserialization.
Vulnerability Repair
The false parameter passed in when instantiating SimpleParser prevents validation of XML format.
Author
Smi1e@WEBIN.LAB - DBAPPSecurity